Today, we're releasing Tenzir Platform v1.10, which introduces a restructed page layout and the ability to statically define workspaces in on-prem environments.
Restructured Nodes Page
This release reorganizes the page layout to improve usability and provide a clearer overview of the current state of a Tenzir Node.
We combined the Explorer, Pipelines, and Contexts tabs into a single, top-level Nodes tab. Additionally, we moved the Installed Packages tab from the library into this new Nodes page.
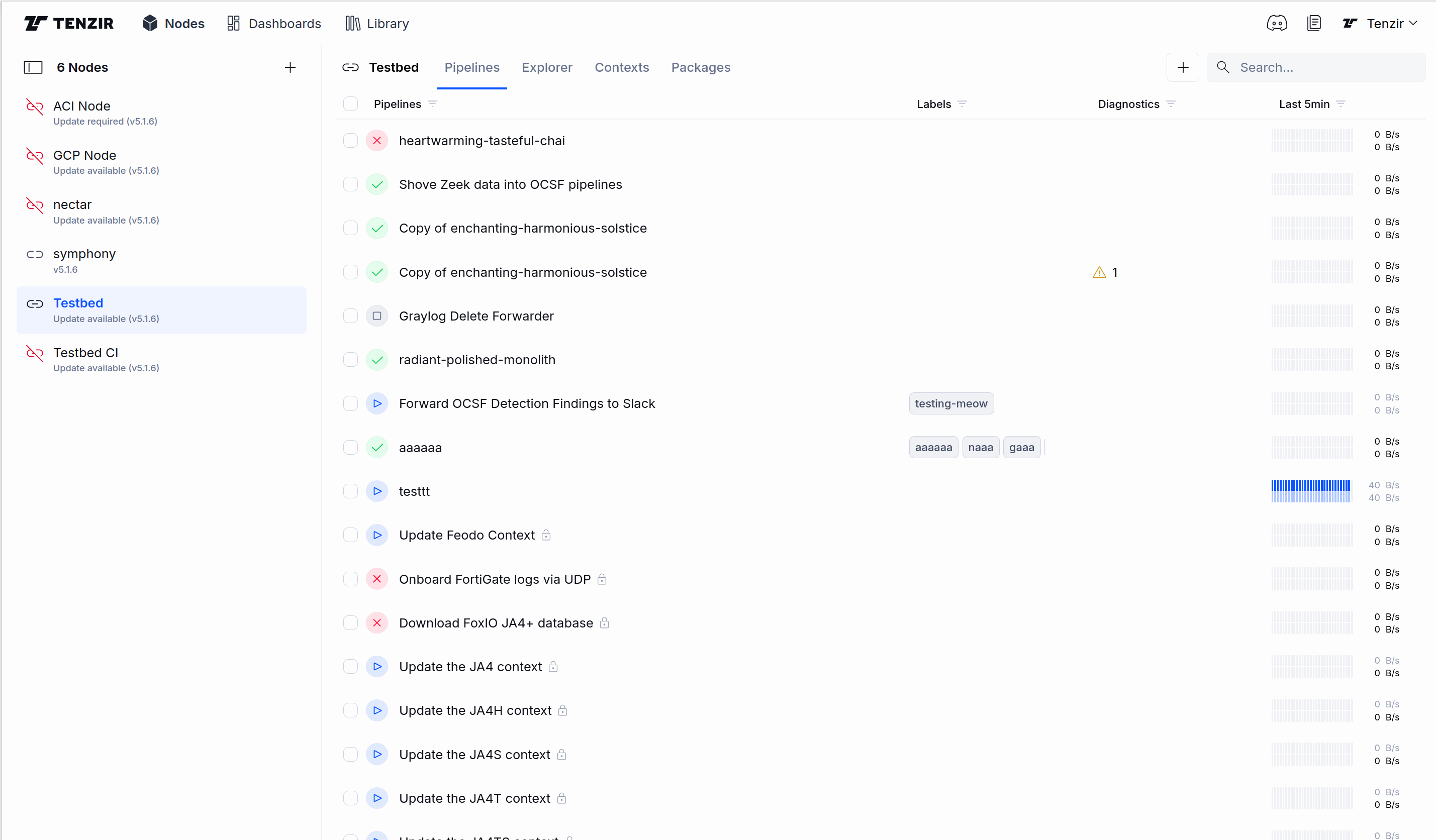
All node-related information is now consolidated on a single page, making it easier to access at a glance.
We plan to add more utilites to the nodes page soon, providing deeper insights into the state of your fleet.
We also redesigned the library, allowing you to filter by the subcategories Sources, Destinations, Mappings and Contexts.
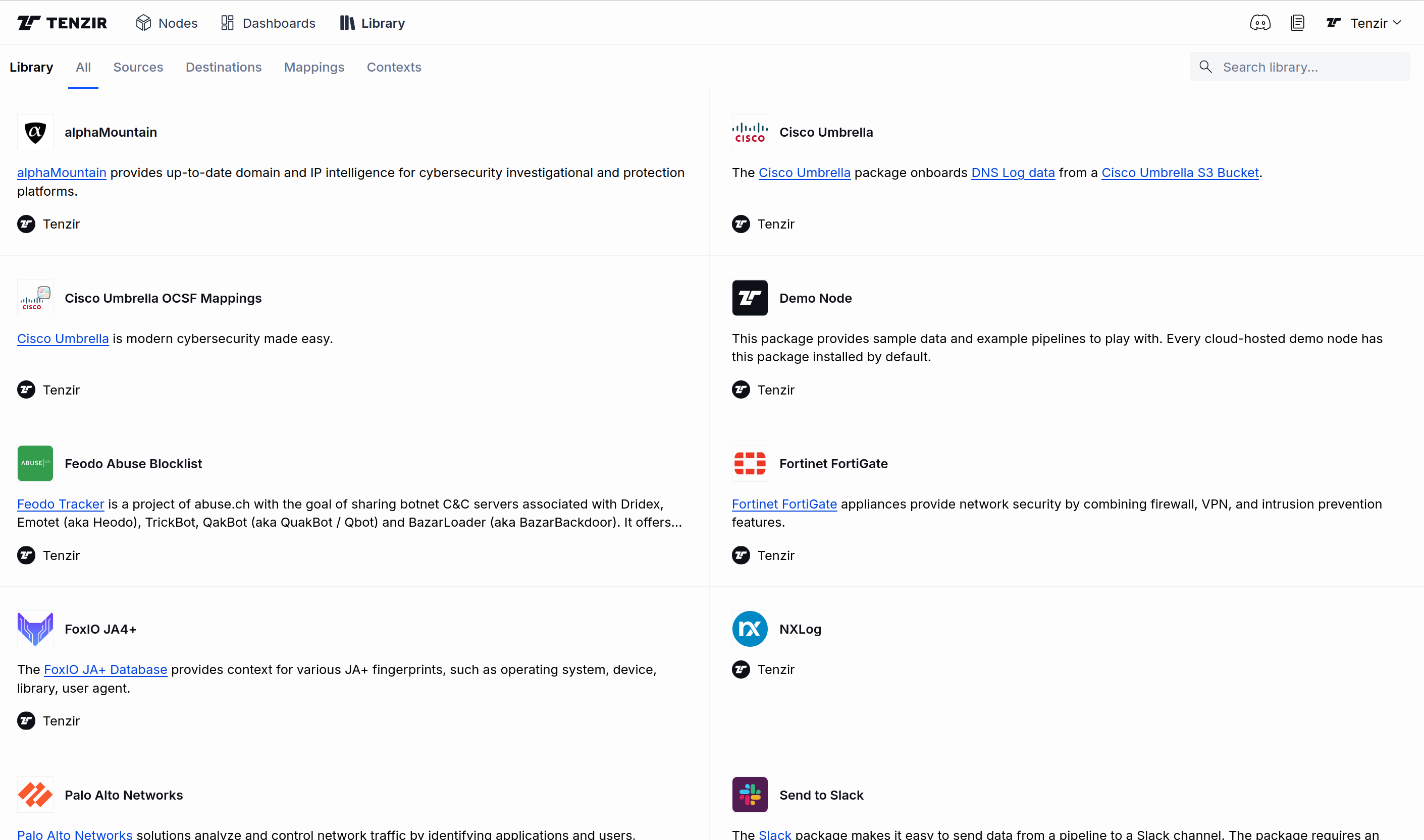
This makes it easier to find exactly the package you're looking for.
Static Workspaces and Ephemeral Nodes
Sovereign Edition users can now define workspaces in a static configuration provided to the Tenzir Platform instance.
---
workspaces:
static0:
name: Tenzir
category: Statically Configured Workspaces
icon-url: https://storage.googleapis.com/tenzir-public-data/icons/tenzir-logo-square.svg
auth-rules:
- {"auth_fn": "auth_allow_all"}
Use the new print-auth-rule CLI command to easily generate auth rules in
the correct format. For example, to get the rule above you can
run tenzir-platform tools print-auth-rule allow-all.
The platform service in a Tenzir Platform deployment uses the WORKSPACE_CONFIG_FILE environment variable to locate the static workspace configuration file.
# docker-compose.yaml
services:
platform:
environment:
# [...]
- WORKSPACE_CONFIG_FILE=/etc/tenzir/workspaces.yaml
volumes:
- ./workspaces.yaml:/etc/tenzir/workspaces.yaml
Ephemeral Nodes
You can define a workspace token for statically configured workspaces. This shared secret allows any Tenzir Node with the token to connect to the workspace.
workspaces:
static0:
token: wsk_e9ee76d4faf4b213745dd5c99a9be11f501d7009ded63f2d5NmDS38vXR
Please note that a valid workspace token must follow a specific format.
To obtain a suitable token for your workspace, use
the tenzir-platform tools generate-workspace-token command.
Instead of writing out the workspace token in plain text, you can specify a file that contains the token:
workspaces:
static0:
token-file: /run/secrets/workspace_token
A Tenzir Node can register itself at the Tenzir Platform dynamically if it knows the workspace token:
$ cat config.yaml
tenzir:
token: wsk_e9ee76d4faf4b213745dd5c99a9be11f501d7009ded63f2d5NmDS38vXR
platform-control-endpoint: http://tenzir-platform.example.org:3001
$ tenzir-node --config=config.yaml
Nodes connected this way are treated as ephemeral, meaning they're not permanently added to the workspace but will disappear as soon as the connection ends.
Static Dashboards
You can define a static set of dashboards for a workspace.
To do so, use the dashboards YAML key:
workspaces:
static0:
dashboards:
dashboard1:
name: Example Dashboard
cells:
- name: Dashboard 1
definition: |
partitions
where not internal
summarize events=sum(events), schema
sort -events
type: table
x: 0
y: 0
w: 12
h: 12
Dashboards are arranged in a virtual grid of width 24. Ensure that
x + w <= 24 when setting dashboard coordinates.
While it is possible to update dashboards defined like this at runtime, they reset to their original state every time the platform restarts.
Other Changes
Infrastructure
- We improved the
localdevexample setup for the Tenzir Platform. It now contains a Tenzir Node that is automatically connected to the local platform instance and a CLI container with admin permissions. Additionally, users of thelocaldevsetup are now granted admin permissions by default. - We fixed a bug in the alerts API that caused configured alerts to be only activated after the next restart of the websocket gateway.
- The new
TENZIR_PLATFORM_METRICS_STORE_S3_BUCKET_NAMEvariable can be set to a valid S3 bucket name. If set, the platform stores all pipeline metrics it receives from connected Tenzir Nodes into this bucket.
Frontend
- The URL format was changed and now contains the workspace id, making it easier to share Tenzir Platform URLs with other users. NOTE: There is no automatic redirect, so old pipeline share url will not work anymore.
- The y-axis ticks for stacked area and bar charts were fixed.
- Fixed rendering of blobs in the
Data.Blobcomponent. - Added BITZ and TQL as downloadable formats for events.
- Fixed an issue where pie chart colors were sometimes incorrect in the dashboard.
CLI
- We replaced the
--dry-runoption for thetenzir-platform admin add-auth-rulecommands with the newtenzir-platform tools print-auth-rulecommands. - The Tenzir Platform CLI now automatically authenticates using the client credentials flow when a client secret is provided as environment variable.
- The Tenzir Platform CLI now supports device code flow authentication for IdP's without a complete verification URL (like Microsoft Entra)
Join Us for Office Hours
Join us for our bi-weekly office hours every other Tuesday at 5 PM CET on our Discord server. It's a great opportunity to share your experiences, ask questions, and help shape the future of Tenzir with your valuable feedback!
